Comparing SQL Constraints for Better Data Integrity

Maintaining data integrity stands as a top priority for any organization relying on relational databases. Constraints in sql serve as a powerful safeguard, ensuring that only valid and consistent data enters the system.
Constraints in sql directly enforce business rules at the database level, reducing the chance of data errors even if application checks fail.
SQL constraints make the schema explicit, helping teams maintain consistent data as applications evolve or multiple users interact with the database.
SQL provides a critical safety net, preventing data corruption and making failing transactions preferable to storing invalid information.
These practices help organizations achieve reliable, high-quality data that supports critical operations.
Key Takeaways
SQL constraints like NOT NULL, UNIQUE, PRIMARY KEY, FOREIGN KEY, CHECK, and DEFAULT protect data by enforcing rules directly in the database.
Primary keys uniquely identify records and support relationships, while unique constraints ensure distinct values but allow some nulls.
Foreign key constraints keep data linked across tables, preventing orphaned or invalid records and maintaining consistency.
Check constraints enforce business rules by limiting allowed values, and default constraints provide automatic values when none are given.
Using tools like Chat2DB simplifies creating and managing constraints with AI and visual aids, helping teams keep data accurate and reliable.
Different Types of Constraints in SQL
Modern databases rely on different types of constraints to maintain accurate and reliable data. Each constraint in SQL serves a unique purpose, ensuring that the database enforces rules automatically and consistently.
NOT NULL
The not null constraint requires that a column always contains a value. This prevents missing or incomplete data in critical fields. For example, in a customer table, applying NOT NULL to the email column ensures every customer record includes an email address.
CREATE TABLE Customers (
CustomerID INT PRIMARY KEY,
Email VARCHAR(255) NOT NULL
);
This constraint enhances data integrity by guaranteeing that essential information is never left blank.
UNIQUE
The unique constraint ensures that all values in a column or set of columns remain distinct. It prevents duplicate entries, which is vital for fields like usernames or serial numbers.
ALTER TABLE Products ADD CONSTRAINT unique_sku UNIQUE (SKU);
By enforcing uniqueness, this constraint supports accurate identification and reduces data redundancy.
PRIMARY KEY
A primary key constraint combines the effects of NOT NULL and UNIQUE. It uniquely identifies each row in a table and enforces entity integrity. Only one primary key exists per table, and it cannot accept null values.
CREATE TABLE Orders (
OrderID INT PRIMARY KEY,
OrderDate DATE
);
This constraint forms the backbone of relational databases, supporting reliable relationships between tables.
FOREIGN KEY Constraint
The foreign key constraint links a column in one table to the primary key in another, maintaining referential integrity. It ensures that data in the child table corresponds to valid entries in the parent table.
CREATE TABLE OrderItems (
ItemID INT PRIMARY KEY,
OrderID INT,
FOREIGN KEY (OrderID) REFERENCES Orders(OrderID)
);
This constraint prevents orphaned records and enforces valid relationships across tables.
CHECK
A check constraint enforces business rules by limiting the values allowed in a column. For example, it can ensure that a salary falls within a specific range or that a quantity is always positive.
ALTER TABLE Employees ADD CONSTRAINT check_salary CHECK (Salary BETWEEN 30000 AND 100000);
By embedding business logic at the database level, check constraints protect data quality regardless of how data enters the system.
DEFAULT
The default constraint assigns a standard value to a column when no value is provided during insertion. This automation ensures consistent data entry and reduces manual errors.
CREATE TABLE Tasks (
TaskID INT PRIMARY KEY,
Status VARCHAR(20) DEFAULT 'Pending'
);
Default constraints prove especially useful in transactional systems, where certain fields often require the same initial value.
Tip: Combining different types of constraints in SQL creates a robust safety net, ensuring that every aspect of data entry and modification aligns with business requirements.
How Constraints in SQL Ensure Data Integrity
Preventing Invalid Data
Constraints in sql play a crucial role in blocking invalid or inconsistent data before it enters the database. SQL check constraint rules validate each new row and reject any data that does not meet the specified criteria. Unique constraints ensure that columns like email or username do not contain duplicate values. These mechanisms work even when application-level checks fail or users bypass front-end validation.
SQL check constraint can enforce phone number formats, allowing only numeric entries of a certain length.
Unique constraints prevent duplicate serial numbers or IDs.
Salary range restrictions, set with a check constraint, stop unrealistic values from being stored.
File extension validations ensure only proper file types are accepted.
By enforcing these rules at the database level, sql maintains domain integrity and reduces the frequency of invalid data entries in production environments.
Enforcing Relationships
SQL maintains referential integrity between tables using the foreign key constraint. This constraint links records in one table to valid entries in another, ensuring that relationships remain consistent. In large-scale systems, foreign key constraint definitions and procedural enforcement through triggers or stored procedures help maintain these links. When a user inserts or updates data, the database checks both parent and child tables to confirm that all references are valid. This process prevents orphaned records and guarantees that every relationship follows the intended structure. By handling these checks within the database, sql ensures that all applications accessing the data follow the same rules, making referential integrity robust and reliable.
Supporting Business Rules
SQL constraints enforce a wide range of business rules directly within the database. The following table highlights common constraint types and the business logic they support:
Constraint Type | Business Rule Enforced | Description and Effectiveness |
|---|---|---|
NOT NULL | Mandatory data presence | Ensures essential fields are never left blank, supporting data completeness. |
UNIQUE | Uniqueness of data | Prevents duplicate entries, useful for identifiers and codes. |
PRIMARY KEY | Unique record identification | Guarantees each row is distinct, critical for indexing and relational integrity. |
FOREIGN KEY | Referential integrity between tables | Maintains consistent links between related tables. |
CHECK | Domain-specific validations | Enforces custom rules, such as value ranges or formats, supporting business logic. |
DEFAULT | Default values for columns | Assigns standard values automatically, reducing manual errors. |
SQL constraints and triggers improve data reliability and reduce the need for complex application logic. While some environments may limit constraint use, these features remain highly effective for enforcing business requirements and maintaining data quality.
Comparing SQL Constraints
PRIMARY KEY vs UNIQUE
Database designers often face the decision of whether to use a primary key constraint or a unique constraint for ensuring row uniqueness. Both constraints in sql enforce uniqueness, but they serve different roles and have distinct behaviors.
The primary key constraint uniquely identifies each row and does not allow NULL values. It acts as the main identifier for table records and supports entity integrity.
Unique constraints also enforce uniqueness but permit NULL values, which can result in multiple rows with NULL in the same column.
Both constraints create unique indexes, improving query performance. However, only the primary key constraint automatically becomes the target for foreign key relationships.
Unique constraints maintain data integrity for columns that require distinct values but do not serve as the main row identifier.
Note: Using a primary key constraint is essential for tables that participate in relationships, as it enables referential integrity through foreign key constraint definitions.
The following table summarizes key differences, especially for composite keys:
Aspect | PRIMARY KEY Constraint | UNIQUE Constraint |
|---|---|---|
Uniqueness | Enforces uniqueness and non-nullability | Enforces uniqueness, allows multiple NULLs |
Main Identifier | Yes | No |
Foreign Key Target | Yes | No |
Indexing | Automatically indexed | Indexed |
Composite Key Use | Used when no single column is unique | Used for additional uniqueness, not as main key |
ORM Compatibility | More complex with composite keys | Easier with single-column primary keys |
Example |
| Unique constraint on |
Experts recommend using a single-column primary key for simplicity and maintainability. Composite primary keys can complicate relationships and increase storage overhead. Unique constraints provide flexibility for enforcing uniqueness on other columns without the complexity of composite keys.
FOREIGN KEY Constraint and Relational Integrity
The foreign key constraint plays a critical role in maintaining referential integrity between tables in sql. It ensures that a value in one table matches a valid entry in another, preventing orphaned records and data inconsistencies.
Common issues with foreign key constraint implementation include:
Mismatched data types between referencing and referenced columns, which can cause errors.
Dangling foreign keys due to schema changes or incorrect creation order.
Lack of indexes on foreign key columns, leading to poor query performance.
Circular references that complicate insertions and deletions.
Performance overhead in large databases with frequent updates or deletions.
Constraint violations when deleting or updating referenced records.
Indexing foreign key columns to optimize joins and queries.
Using cascading actions like
ON DELETE CASCADEto manage related data efficiently.Avoiding circular references or using deferred constraints.
Batching large operations to reduce performance impact.
Tip: Always declare foreign key constraints at the database level to enforce referential integrity and prevent data corruption. Application-level enforcement is more error-prone and resource-intensive.
In high-transaction environments, foreign key constraints can introduce latency due to locking and additional row lookups. For example, inserting a row in a child table may lock the parent row, causing delays under heavy load. Distributed systems may implement foreign key logic at the middleware level to improve scalability, but this adds complexity. A hybrid approach can balance performance and data integrity, depending on application needs.
CHECK vs DEFAULT
The check constraint and default constraint both contribute to data quality, but they serve different purposes in sql.
The check constraint enforces business rules by validating that data meets specific conditions or falls within a defined range. For example, it can restrict an age column to values between 18 and 120. If a value outside this range is inserted, the database rejects it.
The default constraint assigns a predefined value to a column when no explicit value is provided during insertion. For instance, a status column might default to 'Pending' if not specified.
Key differences include:
The check constraint actively prevents invalid data by rejecting out-of-range or incorrect values.
The default constraint only supplies a value when none is provided, but does not validate or restrict values if one is supplied explicitly.
Note: Best practices recommend using a check constraint to enforce value ranges or patterns, especially when multiple applications or users modify the data. This ensures consistent enforcement of business rules at the database level.
Check constraints are ideal for simple, stable validations, such as restricting a flag column to 'Y' or 'N'. They help prevent data corruption and can improve query performance by allowing the optimizer to exclude impossible values. Default constraints simplify data entry and maintain consistency but do not enforce data correctness.
Practical Decision-Making for Database Design
Choosing the right constraints in sql depends on the specific requirements of the application:
Use a primary key constraint for the main identifier of each table to ensure entity integrity and support foreign key relationships.
Apply unique constraints to columns that require distinct values but do not serve as the main identifier.
Implement foreign key constraints to maintain referential integrity and prevent orphaned records.
Use check constraints to enforce business rules and value ranges directly in the database.
Set default constraints to automate common values and reduce manual errors, but always pair them with validation if data correctness is critical.
Common Pitfall: Relying solely on application logic for data validation can lead to inconsistencies. Enforcing rules with sql constraints ensures data integrity regardless of how data enters the system.
Modern tools like Chat2DB streamline the process of defining, managing, and visualizing these constraints. Chat2DB supports a wide range of databases and provides AI-powered SQL generation, making it easier for teams to implement robust data integrity measures without deep SQL expertise. Its visual interface helps users spot constraint issues early, while its security features ensure safe management of sensitive data.
Real-World Use Case
Learning Management System Example
A Learning Management System (LMS) manages students, courses, enrollments, and grades. In such a system, sql constraints play a vital role in maintaining data integrity across multiple tables. Each student and course receives a unique identifier through a primary key. The foreign key constraint links enrollments to both students and courses, ensuring that every enrollment references valid records. This prevents orphaned enrollments and maintains consistent relationships.
A not null constraint on essential fields like student names or course titles guarantees that critical information is always present. The unique constraint on email addresses avoids duplicate student accounts, which is crucial for user management. The check constraint enforces business rules, such as restricting grades to a valid range (for example, 0 to 100). The default constraint can set an initial status for new enrollments, such as 'active,' reducing manual input errors.
Together, these constraints ensure that the LMS database remains accurate, consistent, and reliable, even as the system scales or multiple users interact with it.
Constraint Type | Role in LMS Schema |
|---|---|
Primary Key | Uniquely identifies students, courses, and enrollments |
Foreign Key | Maintains referential integrity between enrollments, students, and courses |
Unique Constraint | Prevents duplicate emails or course codes |
Check Constraint | Validates grade ranges and enrollment statuses |
Default Constraint | Sets standard values for new records, such as default enrollment status |
Combining Constraints for Robustness
Combining multiple sql constraints in a complex LMS environment delivers measurable benefits. Automated enforcement of data rules reduces manual database operations by up to 70%. Teams implement changes 60% faster and experience 80% fewer deployment-related incidents. The integration of constraints, automation, and monitoring leads to more effective collaboration and fewer environment-related issues.
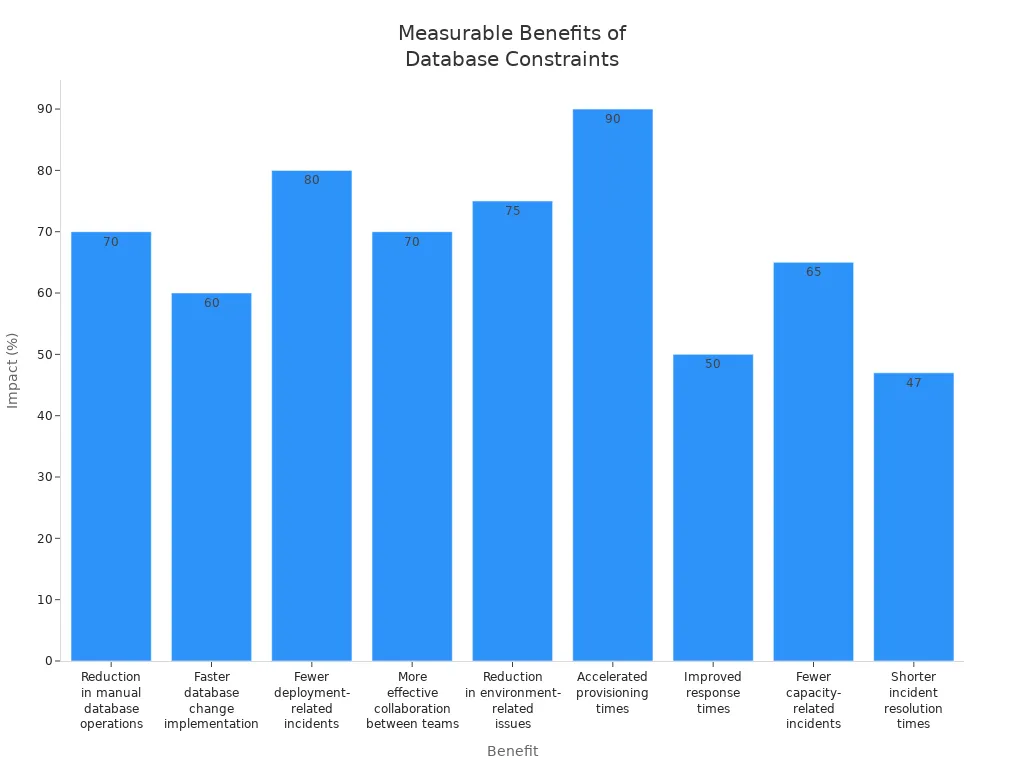
Foreign key constraint ensures that every enrollment always references a valid student and course.
Unique constraints on user emails prevent duplicate accounts, supporting secure authentication.
Check constraint validates that grades and statuses remain within acceptable values.
Default constraint streamlines data entry by providing initial values for new records.
These practices create a robust safety net, minimizing errors and supporting scalable, maintainable database design. By leveraging sql constraints, organizations can trust the integrity of their LMS data, even as requirements evolve.
Best Practices for Constraints in SQL
Choosing the Right Constraints
Selecting the appropriate constraints in sql forms the foundation of a reliable database. Database designers should evaluate each table and column to determine which rules best protect data quality. The following criteria help guide this process:
Assess the need for primary keys, unique keys, foreign keys, and not null constraints based on the data model and relationships.
Ensure that each primary key remains unique and not null, supporting fast data retrieval and clear identification.
Use foreign keys to define relationships, making sure the referenced columns in the parent table have a primary or unique key.
Apply check constraint rules to enforce business logic, such as value ranges or specific formats.
Normalize tables to reduce redundancy and use foreign keys for linking related data.
Consider performance by indexing columns involved in constraints, especially those used in queries.
Plan for future growth by designing scalable keys and testing the database structure thoroughly.
Confirm that the database privileges allow for constraint creation and management.
Adding constraints not only improves data integrity but also clarifies the data model. Business intelligence tools can leverage these definitions for automatic joins and query optimization.
Tip: Automatic constraint generation can be enabled or disabled depending on project needs, allowing flexibility during development.
Common Mistakes to Avoid
Many developers encounter pitfalls when implementing sql constraints. Awareness of these common mistakes helps maintain a robust database:
1. Failing to add a check constraint for data validation, which can lead to invalid or inconsistent entries. 2. Overlooking indexes on foreign keys or frequently queried columns, resulting in slower performance and weaker constraint enforcement. 3. Neglecting referential integrity by omitting foreign key constraints, which may cause orphaned records. 4. Using natural keys as primary keys, which can change over time and disrupt relationships; surrogate keys offer greater stability. 5. Ignoring normalization principles, leading to redundant data and maintenance challenges. 6. Inserting or updating data without proper validation, which can introduce inconsistencies.
Note: Enforcing constraints at the database level ensures that all applications and users follow the same rules, reducing the risk of errors.
Chat2DB supports best practices by providing visual tools and AI-powered sql generation. Users can define, review, and manage constraints efficiently, ensuring that every check constraint, key, and relationship aligns with business requirements. The platform’s compatibility with multiple databases and its intuitive interface make it easier to avoid common mistakes and maintain data integrity.
Managing Constraints with Chat2DB
Modern database teams face increasing complexity when managing sql constraints across diverse environments. Chat2DB streamlines this process by combining artificial intelligence with intuitive visual tools, making constraint management faster and more reliable for users of all skill levels.
AI-Powered SQL Generation
Chat2DB leverages advanced AI to simplify sql constraint creation and maintenance. The platform’s Text2SQL feature allows users to describe their requirements in plain language. The AI then generates precise sql statements, reducing manual coding and minimizing errors. Users benefit from:
An AI SQL Editor and Query Generator that handle complex constraint logic with ease.
A context-aware AI chatbot that assists with sql syntax and best practices.
One-click SQL error fixes, which help resolve issues quickly, even for constraint-related errors.
Code generation from database schemas, accelerating the implementation of new constraints.
Customizable business terms in AI column comments, enabling the AI to generate optimized sql queries tailored to specific organizational needs.
These features empower teams to implement and adjust sql constraints efficiently, supporting both rapid development and ongoing maintenance.
Visual Database Management
Chat2DB enhances accuracy and efficiency through its visual database management capabilities. The platform provides a visual schema exploration interface, allowing users to see exactly where constraints apply within their databases. Key benefits include:
Intuitive mapping of constraints, which helps users understand relationships and dependencies at a glance.
Automated constraint validation tools that check each sql constraint against defined rules, ensuring correct implementation.
A query builder that enables safe testing of constraints in a sandbox environment before deployment.
Automated documentation generation, which keeps records of all constraint definitions organized and accessible.
Performance monitoring tools that help identify and optimize constraint-related bottlenecks.
A recent case study showed a development team using Chat2DB’s AI and visual tools to quickly implement and optimize check constraints. The result was improved data integrity and better overall database performance.
Chat2DB supports a wide range of relational and non-relational databases, making it a versatile solution for organizations with diverse data needs. Security remains a top priority, with features like local query processing, encryption, and robust access controls. Teams can collaborate seamlessly, sharing dashboards and insights while maintaining strict data privacy.
By integrating AI-powered sql generation with visual management tools, Chat2DB helps users enforce data integrity, reduce errors, and streamline database operations.
SQL constraints such as NOT NULL, UNIQUE, PRIMARY KEY, FOREIGN KEY, CHECK, and DEFAULT form the backbone of reliable data integrity. Database professionals should define these rules early, use meaningful names, and regularly review them to match evolving needs. Combining multiple constraints ensures comprehensive protection against errors. For efficient management, teams can leverage tools like Chat2DB, which streamlines constraint creation, supports diverse databases, and accelerates query optimization.
Start by reviewing your current schema, document constraint logic, and adopt automated tools to maintain robust, self-regulating databases.
FAQ
What is the main difference between a PRIMARY KEY and a UNIQUE constraint?
A PRIMARY KEY uniquely identifies each row and does not allow NULL values. A UNIQUE constraint also enforces uniqueness but permits multiple NULLs. Both improve data integrity, but only PRIMARY KEY supports table relationships.
Can I use multiple constraints on a single column?
Yes. You can combine constraints like NOT NULL, UNIQUE, and CHECK on one column. This approach strengthens data validation and ensures that each rule enforces a specific aspect of data integrity.
How do SQL constraints help prevent data errors?
SQL constraints automatically block invalid, duplicate, or inconsistent data before it enters the database. They enforce business rules at the database level, reducing manual checks and minimizing the risk of data corruption.
How does Chat2DB assist with managing SQL constraints?
Chat2DB provides AI-powered SQL generation and visual management tools. Users can define, review, and optimize constraints across multiple databases. The platform simplifies constraint creation, reduces errors, and supports both technical and non-technical users in maintaining data integrity.
See Also
Improving Database Efficiency Through High And Low Cardinality
How To Effectively Convert Text To SQL Using LLMs
Complete 2025 Overview Of SQL DDL And DML Commands
Essential Strategies For Optimizing SQL Queries Successfully

